How America Took Out The Nord Stream Pipeline
The New York Times called it a “mystery,” but the United States executed a covert sea operation that was kept secret—until now

The U.S. Navy’s Diving and Salvage Center can be found in a location as obscure as its name—down what was once a country lane in rural Panama City, a now-booming resort city in the southwestern panhandle of Florida, 70 miles south of the Alabama border. The center’s complex is as nondescript as its location—a drab concrete post-World War II structure that has the look of a vocational high school on the west side of Chicago. A coin-operated laundromat and a dance school are across what is now a four-lane road.
The center has been training highly skilled deep-water divers for decades who, once assigned to American military units worldwide, are capable of technical diving to do the good—using C4 explosives to clear harbors and beaches of debris and unexploded ordinance—as well as the bad, like blowing up foreign oil rigs, fouling intake valves for undersea power plants, destroying locks on crucial shipping canals. The Panama City center, which boasts the second largest indoor pool in America, was the perfect place to recruit the best, and most taciturn, graduates of the diving school who successfully did last summer what they had been authorized to do 260 feet under the surface of the Baltic Sea.
Last June, the Navy divers, operating under the cover of a widely publicized mid-summer NATO exercise known as BALTOPS 22, planted the remotely triggered explosives that, three months later, destroyed three of the four Nord Stream pipelines, according to a source with direct knowledge of the operational planning.
Two of the pipelines, which were known collectively as Nord Stream 1, had been providing Germany and much of Western Europe with cheap Russian natural gas for more than a decade. A second pair of pipelines, called Nord Stream 2, had been built but were not yet operational. Now, with Russian troops massing on the Ukrainian border and the bloodiest war in Europe since 1945 looming, President Joseph Biden saw the pipelines as a vehicle for Vladimir Putin to weaponize natural gas for his political and territorial ambitions.
Asked for comment, Adrienne Watson, a White House spokesperson, said in an email, “This is false and complete fiction.” Tammy Thorp, a spokesperson for the Central Intelligence Agency, similarly wrote: “This claim is completely and utterly false.”
Biden’s decision to sabotage the pipelines came after more than nine months of highly secret back and forth debate inside Washington’s national security community about how to best achieve that goal. For much of that time, the issue was not whether to do the mission, but how to get it done with no overt clue as to who was responsible.
There was a vital bureaucratic reason for relying on the graduates of the center’s hardcore diving school in Panama City. The divers were Navy only, and not members of America’s Special Operations Command, whose covert operations must be reported to Congress and briefed in advance to the Senate and House leadership—the so-called Gang of Eight. The Biden Administration was doing everything possible to avoid leaks as the planning took place late in 2021 and into the first months of 2022.
President Biden and his foreign policy team—National Security Adviser Jake Sullivan, Secretary of State Tony Blinken, and Victoria Nuland, the Undersecretary of State for Policy—had been vocal and consistent in their hostility to the two pipelines, which ran side by side for 750 miles under the Baltic Sea from two different ports in northeastern Russia near the Estonian border, passing close to the Danish island of Bornholm before ending in northern Germany.
The direct route, which bypassed any need to transit Ukraine, had been a boon for the German economy, which enjoyed an abundance of cheap Russian natural gas—enough to run its factories and heat its homes while enabling German distributors to sell excess gas, at a profit, throughout Western Europe. Action that could be traced to the administration would violate US promises to minimize direct conflict with Russia. Secrecy was essential.
From its earliest days, Nord Stream 1 was seen by Washington and its anti-Russian NATO partners as a threat to western dominance. The holding company behind it, Nord Stream AG, was incorporated in Switzerland in 2005 in partnership with Gazprom, a publicly traded Russian company producing enormous profits for shareholders which is dominated by oligarchs known to be in the thrall of Putin. Gazprom controlled 51 percent of the company, with four European energy firms—one in France, one in the Netherlands and two in Germany—sharing the remaining 49 percent of stock, and having the right to control downstream sales of the inexpensive natural gas to local distributors in Germany and Western Europe. Gazprom’s profits were shared with the Russian government, and state gas and oil revenues were estimated in some years to amount to as much as 45 percent of Russia’s annual budget.
America’s political fears were real: Putin would now have an additional and much-needed major source of income, and Germany and the rest of Western Europe would become addicted to low-cost natural gas supplied by Russia—while diminishing European reliance on America. In fact, that’s exactly what happened. Many Germans saw Nord Stream 1 as part of the deliverance of former Chancellor Willy Brandt’s famed Ostpolitik theory, which would enable postwar Germany to rehabilitate itself and other European nations destroyed in World War II by, among other initiatives, utilizing cheap Russian gas to fuel a prosperous Western European market and trading economy.
Nord Stream 1 was dangerous enough, in the view of NATO and Washington, but Nord Stream 2, whose construction was completed in September of 2021, would, if approved by German regulators, double the amount of cheap gas that would be available to Germany and Western Europe. The second pipeline also would provide enough gas for more than 50 percent of Germany’s annual consumption. Tensions were constantly escalating between Russia and NATO, backed by the aggressive foreign policy of the Biden Administration.
Opposition to Nord Stream 2 flared on the eve of the Biden inauguration in January 2021, when Senate Republicans, led by Ted Cruz of Texas, repeatedly raised the political threat of cheap Russian natural gas during the confirmation hearing of Blinken as Secretary of State. By then a unified Senate had successfully passed a law that, as Cruz told Blinken, “halted [the pipeline] in its tracks.” There would be enormous political and economic pressure from the German government, then headed by Angela Merkel, to get the second pipeline online.
Would Biden stand up to the Germans? Blinken said yes, but added that he had not discussed the specifics of the incoming President’s views. “I know his strong conviction that this is a bad idea, the Nord Stream 2,” he said. “I know that he would have us use every persuasive tool that we have to convince our friends and partners, including Germany, not to move forward with it.”
A few months later, as the construction of the second pipeline neared completion, Biden blinked. That May, in a stunning turnaround, the administration waived sanctions against Nord Stream AG, with a State Department official conceding that trying to stop the pipeline through sanctions and diplomacy had “always been a long shot.” Behind the scenes, administration officials reportedly urged Ukrainian President Volodymyr Zelensky, by then facing a threat of Russian invasion, not to criticize the move.
There were immediate consequences. Senate Republicans, led by Cruz, announced an immediate blockade of all of Biden’s foreign policy nominees and delayed passage of the annual defense bill for months, deep into the fall. Politico later depicted Biden’s turnabout on the second Russian pipeline as “the one decision, arguably more than the chaotic military withdrawal from Afghanistan, that has imperiled Biden’s agenda.”
The administration was floundering, despite getting a reprieve on the crisis in mid-November, when Germany’s energy regulators suspended approval of the second Nord Stream pipeline. Natural gas prices surged 8% within days, amid growing fears in Germany and Europe that the pipeline suspension and the growing possibility of a war between Russia and Ukraine would lead to a very much unwanted cold winter. It was not clear to Washington just where Olaf Scholz, Germany’s newly appointed chancellor, stood. Months earlier, after the fall of Afghanistan, Scholtz had publicly endorsed French President Emmanuel Macron’s call for a more autonomous European foreign policy in a speech in Prague—clearly suggesting less reliance on Washington and its mercurial actions.
Throughout all of this, Russian troops had been steadily and ominously building up on the borders of Ukraine, and by the end of December more than 100,000 soldiers were in position to strike from Belarus and Crimea. Alarm was growing in Washington, including an assessment from Blinken that those troop numbers could be “doubled in short order.”
The administration’s attention once again was focused on Nord Stream. As long as Europe remained dependent on the pipelines for cheap natural gas, Washington was afraid that countries like Germany would be reluctant to supply Ukraine with the money and weapons it needed to defeat Russia.
It was at this unsettled moment that Biden authorized Jake Sullivan to bring together an interagency group to come up with a plan.
All options were to be on the table. But only one would emerge.
PLANNING
In December of 2021, two months before the first Russian tanks rolled into Ukraine, Jake Sullivan convened a meeting of a newly formed task force—men and women from the Joint Chiefs of Staff, the CIA, and the State and Treasury Departments—and asked for recommendations about how to respond to Putin’s impending invasion.
It would be the first of a series of top-secret meetings, in a secure room on a top floor of the Old Executive Office Building, adjacent to the White House, that was also the home of the President’s Foreign Intelligence Advisory Board (PFIAB). There was the usual back and forth chatter that eventually led to a crucial preliminary question: Would the recommendation forwarded by the group to the President be reversible—such as another layer of sanctions and currency restrictions—or irreversible—that is, kinetic actions, which could not be undone?
What became clear to participants, according to the source with direct knowledge of the process, is that Sullivan intended for the group to come up with a plan for the destruction of the two Nord Stream pipelines—and that he was delivering on the desires of the President.

Jake Sullivan.
Over the next several meetings, the participants debated options for an attack. The Navy proposed using a newly commissioned submarine to assault the pipeline directly. The Air Force discussed dropping bombs with delayed fuses that could be set off remotely. The CIA argued that whatever was done, it would have to be covert. Everyone involved understood the stakes. “This is not kiddie stuff,” the source said. If the attack were traceable to the United States, “It’s an act of war.”
At the time, the CIA was directed by William Burns, a mild-mannered former ambassador to Russia who had served as deputy secretary of state in the Obama Administration. Burns quickly authorized an Agency working group whose ad hoc members included—by chance—someone who was familiar with the capabilities of the Navy’s deep-sea divers in Panama City. Over the next few weeks, members of the CIA’s working group began to craft a plan for a covert operation that would use deep-sea divers to trigger an explosion along the pipeline.
Something like this had been done before. In 1971, the American intelligence community learned from still undisclosed sources that two important units of the Russian Navy were communicating via an undersea cable buried in the Sea of Okhotsk, on Russia’s Far East Coast. The cable linked a regional Navy command to the mainland headquarters at Vladivostok.
A hand-picked team of Central Intelligence Agency and National Security Agency operatives was assembled somewhere in the Washington area, under deep cover, and worked out a plan, using Navy divers, modified submarines and a deep-submarine rescue vehicle, that succeeded, after much trial and error, in locating the Russian cable. The divers planted a sophisticated listening device on the cable that successfully intercepted the Russian traffic and recorded it on a taping system.
The NSA learned that senior Russian navy officers, convinced of the security of their communication link, chatted away with their peers without encryption. The recording device and its tape had to be replaced monthly and the project rolled on merrily for a decade until it was compromised by a forty-four-year-old civilian NSA technician named Ronald Pelton who was fluent in Russian. Pelton was betrayed by a Russian defector in 1985 and sentenced to prison. He was paid just $5,000 by the Russians for his revelations about the operation, along with $35,000 for other Russian operational data he provided that was never made public.
That underwater success, codenamed Ivy Bells, was innovative and risky, and produced invaluable intelligence about the Russian Navy's intentions and planning.
Still, the interagency group was initially skeptical of the CIA’s enthusiasm for a covert deep-sea attack. There were too many unanswered questions. The waters of the Baltic Sea were heavily patrolled by the Russian navy, and there were no oil rigs that could be used as cover for a diving operation. Would the divers have to go to Estonia, right across the border from Russia’s natural gas loading docks, to train for the mission? “It would be a goat fuck,” the Agency was told.
Throughout “all of this scheming,” the source said, “some working guys in the CIA and the State Department were saying, ‘Don’t do this. It’s stupid and will be a political nightmare if it comes out.’”
Nevertheless, in early 2022, the CIA working group reported back to Sullivan’s interagency group: “We have a way to blow up the pipelines.”
What came next was stunning. On February 7, less than three weeks before the seemingly inevitable Russian invasion of Ukraine, Biden met in his White House office with German Chancellor Olaf Scholz, who, after some wobbling, was now firmly on the American team. At the press briefing that followed, Biden defiantly said, “If Russia invades . . . there will be no longer a Nord Stream 2. We will bring an end to it.”
Twenty days earlier, Undersecretary Nuland had delivered essentially the same message at a State Department briefing, with little press coverage. “I want to be very clear to you today,” she said in response to a question. “If Russia invades Ukraine, one way or another Nord Stream 2 will not move forward.”
Several of those involved in planning the pipeline mission were dismayed by what they viewed as indirect references to the attack.
“It was like putting an atomic bomb on the ground in Tokyo and telling the Japanese that we are going to detonate it,” the source said. “The plan was for the options to be executed post invasion and not advertised publicly. Biden simply didn’t get it or ignored it.”
Biden’s and Nuland’s indiscretion, if that is what it was, might have frustrated some of the planners. But it also created an opportunity. According to the source, some of the senior officials of the CIA determined that blowing up the pipeline “no longer could be considered a covert option because the President just announced that we knew how to do it.”
The plan to blow up Nord Stream 1 and 2 was suddenly downgraded from a covert operation requiring that Congress be informed to one that was deemed as a highly classified intelligence operation with U.S. military support. Under the law, the source explained, “There was no longer a legal requirement to report the operation to Congress. All they had to do now is just do it—but it still had to be secret. The Russians have superlative surveillance of the Baltic Sea.”
The Agency working group members had no direct contact with the White House, and were eager to find out if the President meant what he’d said—that is, if the mission was now a go. The source recalled, “Bill Burns comes back and says, ‘Do it.’”
“The Norwegian navy was quick to find the right spot, in the shallow water a few miles off Denmark’s Bornholm Island . . .”
THE OPERATION
Norway was the perfect place to base the mission.
In the past few years of East-West crisis, the U.S. military has vastly expanded its presence inside Norway, whose western border runs 1,400 miles along the north Atlantic Ocean and merges above the Arctic Circle with Russia. The Pentagon has created high paying jobs and contracts, amid some local controversy, by investing hundreds of millions of dollars to upgrade and expand American Navy and Air Force facilities in Norway. The new works included, most importantly, an advanced synthetic aperture radar far up north that was capable of penetrating deep into Russia and came online just as the American intelligence community lost access to a series of long-range listening sites inside China.
A newly refurbished American submarine base, which had been under construction for years, had become operational and more American submarines were now able to work closely with their Norwegian colleagues to monitor and spy on a major Russian nuclear redoubt 250 miles to the east, on the Kola Peninsula. America also has vastly expanded a Norwegian air base in the north and delivered to the Norwegian air force a fleet of Boeing-built P8 Poseidon patrol planes to bolster its long-range spying on all things Russia.
In return, the Norwegian government angered liberals and some moderates in its parliament last November by passing the Supplementary Defense Cooperation Agreement (SDCA). Under the new deal, the U.S. legal system would have jurisdiction in certain “agreed areas” in the North over American soldiers accused of crimes off base, as well as over those Norwegian citizens accused or suspected of interfering with the work at the base.
Norway was one of the original signatories of the NATO Treaty in 1949, in the early days of the Cold War. Today, the supreme commander of NATO is Jens Stoltenberg, a committed anti-communist, who served as Norway’s prime minister for eight years before moving to his high NATO post, with American backing, in 2014. He was a hardliner on all things Putin and Russia who had cooperated with the American intelligence community since the Vietnam War. He has been trusted completely since. “He is the glove that fits the American hand,” the source said.
Back in Washington, planners knew they had to go to Norway. “They hated the Russians, and the Norwegian navy was full of superb sailors and divers who had generations of experience in highly profitable deep-sea oil and gas exploration,” the source said. They also could be trusted to keep the mission secret. (The Norwegians may have had other interests as well. The destruction of Nord Stream—if the Americans could pull it off—would allow Norway to sell vastly more of its own natural gas to Europe.)
Sometime in March, a few members of the team flew to Norway to meet with the Norwegian Secret Service and Navy. One of the key questions was where exactly in the Baltic Sea was the best place to plant the explosives. Nord Stream 1 and 2, each with two sets of pipelines, were separated much of the way by little more than a mile as they made their run to the port of Greifswald in the far northeast of Germany.
The Norwegian navy was quick to find the right spot, in the shallow waters of the Baltic sea a few miles off Denmark’s Bornholm Island. The pipelines ran more than a mile apart along a seafloor that was only 260 feet deep. That would be well within the range of the divers, who, operating from a Norwegian Alta class mine hunter, would dive with a mixture of oxygen, nitrogen and helium streaming from their tanks, and plant shaped C4 charges on the four pipelines with concrete protective covers. It would be tedious, time consuming and dangerous work, but the waters off Bornholm had another advantage: there were no major tidal currents, which would have made the task of diving much more difficult.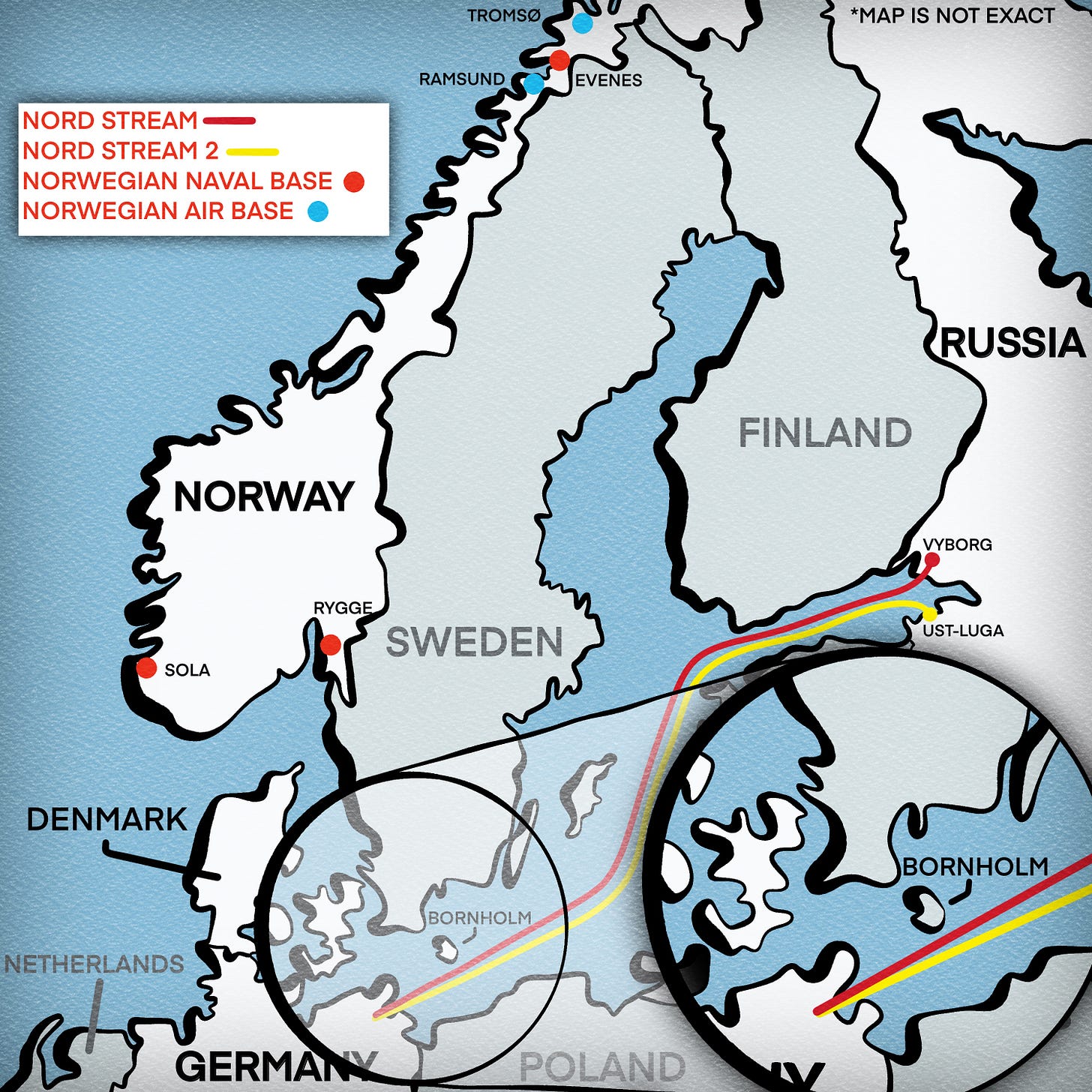
After a bit of research, the Americans were all in.
At this point, the Navy’s obscure deep-diving group in Panama City once again came into play. The deep-sea schools at Panama City, whose trainees participated in Ivy Bells, are seen as an unwanted backwater by the elite graduates of the Naval Academy in Annapolis, who typically seek the glory of being assigned as a Seal, fighter pilot, or submariner. If one must become a “Black Shoe”—that is, a member of the less desirable surface ship command—there is always at least duty on a destroyer, cruiser or amphibious ship. The least glamorous of all is mine warfare. Its divers never appear in Hollywood movies, or on the cover of popular magazines.
“The best divers with deep diving qualifications are a tight community, and only the very best are recruited for the operation and told to be prepared to be summoned to the CIA in Washington,” the source said.
The Norwegians and Americans had a location and the operatives, but there was another concern: any unusual underwater activity in the waters off Bornholm might draw the attention of the Swedish or Danish navies, which could report it.
Denmark had also been one of the original NATO signatories and was known in the intelligence community for its special ties to the United Kingdom. Sweden had applied for membership into NATO, and had demonstrated its great skill in managing its underwater sound and magnetic sensor systems that successfully tracked Russian submarines that would occasionally show up in remote waters of the Swedish archipelago and be forced to the surface.
The Norwegians joined the Americans in insisting that some senior officials in Denmark and Sweden had to be briefed in general terms about possible diving activity in the area. In that way, someone higher up could intervene and keep a report out of the chain of command, thus insulating the pipeline operation. “What they were told and what they knew were purposely different,” the source told me. (The Norwegian embassy, asked to comment on this story, did not respond.)
The Norwegians were key to solving other hurdles. The Russian navy was known to possess surveillance technology capable of spotting, and triggering, underwater mines. The American explosive devices needed to be camouflaged in a way that would make them appear to the Russian system as part of the natural background—something that required adapting to the specific salinity of the water. The Norwegians had a fix.
The Norwegians also had a solution to the crucial question of when the operation should take place. Every June, for the past 21 years, the American Sixth Fleet, whose flagship is based in Gaeta, Italy, south of Rome, has sponsored a major NATO exercise in the Baltic Sea involving scores of allied ships throughout the region. The current exercise, held in June, would be known as Baltic Operations 22, or BALTOPS 22. The Norwegians proposed this would be the ideal cover to plant the mines.
The Americans provided one vital element: they convinced the Sixth Fleet planners to add a research and development exercise to the program. The exercise, as made public by the Navy, involved the Sixth Fleet in collaboration with the Navy’s “research and warfare centers.” The at-sea event would be held off the coast of Bornholm Island and involve NATO teams of divers planting mines, with competing teams using the latest underwater technology to find and destroy them.
It was both a useful exercise and ingenious cover. The Panama City boys would do their thing and the C4 explosives would be in place by the end of BALTOPS22, with a 48-hour timer attached. All of the Americans and Norwegians would be long gone by the first explosion.
The days were counting down. “The clock was ticking, and we were nearing mission accomplished,” the source said.
And then: Washington had second thoughts. The bombs would still be planted during BALTOPS, but the White House worried that a two-day window for their detonation would be too close to the end of the exercise, and it would be obvious that America had been involved.
Instead, the White House had a new request: “Can the guys in the field come up with some way to blow the pipelines later on command?”
Some members of the planning team were angered and frustrated by the President’s seeming indecision. The Panama City divers had repeatedly practiced planting the C4 on pipelines, as they would during BALTOPS, but now the team in Norway had to come up with a way to give Biden what he wanted—the ability to issue a successful execution order at a time of his choosing.
Being tasked with an arbitrary, last-minute change was something the CIA was accustomed to managing. But it also renewed the concerns some shared over the necessity, and legality, of the entire operation.
The President’s secret orders also evoked the CIA’s dilemma in the Vietnam War days, when President Johnson, confronted by growing anti-Vietnam War sentiment, ordered the Agency to violate its charter—which specifically barred it from operating inside America—by spying on antiwar leaders to determine whether they were being controlled by Communist Russia.
The agency ultimately acquiesced, and throughout the 1970s it became clear just how far it had been willing to go. There were subsequent newspaper revelations in the aftermath of the Watergate scandals about the Agency’s spying on American citizens, its involvement in the assassination of foreign leaders and its undermining of the socialist government of Salvador Allende.
Those revelations led to a dramatic series of hearings in the mid-1970s in the Senate, led by Frank Church of Idaho, that made it clear that Richard Helms, the Agency director at the time, accepted that he had an obligation to do what the President wanted, even if it meant violating the law.
In unpublished, closed-door testimony, Helms ruefully explained that “you almost have an Immaculate Conception when you do something” under secret orders from a President. “Whether it’s right that you should have it, or wrong that you shall have it, [the CIA] works under different rules and ground rules than any other part of the government.” He was essentially telling the Senators that he, as head of the CIA, understood that he had been working for the Crown, and not the Constitution.
The Americans at work in Norway operated under the same dynamic, and dutifully began working on the new problem—how to remotely detonate the C4 explosives on Biden’s order. It was a much more demanding assignment than those in Washington understood. There was no way for the team in Norway to know when the President might push the button. Would it be in a few weeks, in many months or in half a year or longer?
The C4 attached to the pipelines would be triggered by a sonar buoy dropped by a plane on short notice, but the procedure involved the most advanced signal processing technology. Once in place, the delayed timing devices attached to any of the four pipelines could be accidentally triggered by the complex mix of ocean background noises throughout the heavily trafficked Baltic Sea—from near and distant ships, underwater drilling, seismic events, waves and even sea creatures. To avoid this, the sonar buoy, once in place, would emit a sequence of unique low frequency tonal sounds—much like those emitted by a flute or a piano—that would be recognized by the timing device and, after a pre-set hours of delay, trigger the explosives. (“You want a signal that is robust enough so that no other signal could accidentally send a pulse that detonated the explosives,” I was told by Dr. Theodore Postol, professor emeritus of science, technology and national security policy at MIT. Postol, who has served as the science adviser to the Pentagon’s Chief of Naval Operations, said the issue facing the group in Norway because of Biden’s delay was one of chance: “The longer the explosives are in the water the greater risk there would be of a random signal that would launch the bombs.”)
On September 26, 2022, a Norwegian Navy P8 surveillance plane made a seemingly routine flight and dropped a sonar buoy. The signal spread underwater, initially to Nord Stream 2 and then on to Nord Stream 1. A few hours later, the high-powered C4 explosives were triggered and three of the four pipelines were put out of commission. Within a few minutes, pools of methane gas that remained in the shuttered pipelines could be seen spreading on the water’s surface and the world learned that something irreversible had taken place.
FALLOUT
In the immediate aftermath of the pipeline bombing, the American media treated it like an unsolved mystery. Russia was repeatedly cited as a likely culprit, spurred on by calculated leaks from the White House—but without ever establishing a clear motive for such an act of self-sabotage, beyond simple retribution. A few months later, when it emerged that Russian authorities had been quietly getting estimates for the cost to repair the pipelines, the New York Times described the news as “complicating theories about who was behind” the attack. No major American newspaper dug into the earlier threats to the pipelines made by Biden and Undersecretary of State Nuland.
While it was never clear why Russia would seek to destroy its own lucrative pipeline, a more telling rationale for the President’s action came from Secretary of State Blinken.
Asked at a press conference last September about the consequences of the worsening energy crisis in Western Europe, Blinken described the moment as a potentially good one:
“It’s a tremendous opportunity to once and for all remove the dependence on Russian energy and thus to take away from Vladimir Putin the weaponization of energy as a means of advancing his imperial designs. That’s very significant and that offers tremendous strategic opportunity for the years to come, but meanwhile we’re determined to do everything we possibly can to make sure the consequences of all of this are not borne by citizens in our countries or, for that matter, around the world.”
More recently, Victoria Nuland expressed satisfaction at the demise of the newest of the pipelines. Testifying at a Senate Foreign Relations Committee hearing in late January she told Senator Ted Cruz, “Like you, I am, and I think the Administration is, very gratified to know that Nord Stream 2 is now, as you like to say, a hunk of metal at the bottom of the sea.”
The source had a much more streetwise view of Biden’s decision to sabotage more than 1500 miles of Gazprom pipeline as winter approached. “Well,” he said, speaking of the President, “I gotta admit the guy has a pair of balls. He said he was going to do it, and he did.”
Asked why he thought the Russians failed to respond, he said cynically, “Maybe they want the capability to do the same things the U.S. did.
“It was a beautiful cover story,” he went on. “Behind it was a covert operation that placed experts in the field and equipment that operated on a covert signal.
“The only flaw was the decision to do it.”
Subscribe to Seymour Hersh
Independent reporting from the world's leading investigative journalist
https://seymourhersh.substack.com/p/how-america-took-out-the-nord-stream
__
eof


%20speaks%20at%20a%20press%20conference%20alongside%20Speaker%20of%20the%20House%20Nancy%20Pelosi.jpg)


